Multi-factor authentication means a person is granted access to a website or application only after successfully presenting two or more pieces of evidence (called factors). The most simple example is a password. Do you want to login to your computer? You’d better know the password!
What is wrong with using a password?
A lot! It’s tempting to create simple passwords so that you can remember them easily. The problem with all passwords is that they are easy for hackers to crack. Turkish researcher Ata Hakçıl, who analyzed more than 700 million passwords revealed in numerous data breaches found that 1 in every 135 passwords people use is actually “123456”. But even when they would have used something really difficult to guess, in the end, all passwords can be guessed given enough time to try them all. And computers can try them all really, really fast.
Multi … what
So it is clear that a password alone is not secure. You need other ways to verify and confirm the person with a password is really you. These other ways are called factors. Traditionally the following factors exist:
- Something you know (a password, the name of your first pet)
- Something you have (a phone, a keycard, a USB token)
- Something you are (your fingerprint, an iris scan)
- Somewhere you are (a location via GPS, a connection to a specific network, an IP address)
Many multi-factor authentication techniques rely on passwords as one factor of authentication. The additional verification method is not employed until after the user’s password has been verified. With MFA, even if a strong user password is compromised, the attacker can not complete the sign-in without also providing more factors.
2-factor (2FA) or multi-factor (MFA)
Although interchangeably used, it is actually just a matter of counting the number of factors you are required to present. Multi-factor just means 2 or more. The more factors required, the more secure but also the less user-friendly it is.
MFA in Azure and Office 365
All your accounts in Office 365 (which is actually Azure AD) can and should be set to use MFA. To make MFA related configuration changes you need to be a Global Admin in your tenant.
The first thing you need to realize is that there is an old, legacy, way to control MFA and there is the modern way to control MFA.
The legacy way, also called ‘per person MFA’ is a settings page where you can enable/disable MFA on a per person level. That doesn’t scale well but it is available for free in all tenants by enabling a feature called ‘Security Defaults’. These settings do work pretty well, but the setup is very basic and it is being replaced by the modern MFA settings in Azure Conditional Access. Microsoft advises to disable these settings and not use them anymore and start using the modern way if your licensing allows it.
The modern way is making MFA a requirement as part of your Conditional Access. Conditional Access requires Azure AD P1 or higher. If your tenant does not hold the licenses “Azure AD Premium P1” or “Azure AD Premium P2” you can not use this.
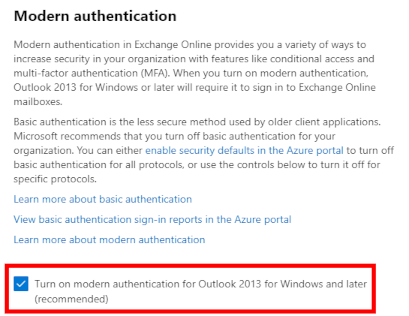
Note: In older tenants, it is required that Modern Authentication is turned on as well. This is the default setting since 2019.
Enabling Modern Authentication
- In the Microsoft 365 admin center, in the left nav choose Settings > Org settings.
- Under Services tab, choose Modern authentication, and in the Modern authentication pane, make sure Enable Modern authentication is selected. Choose Save changes.
Conditional Access in Azure
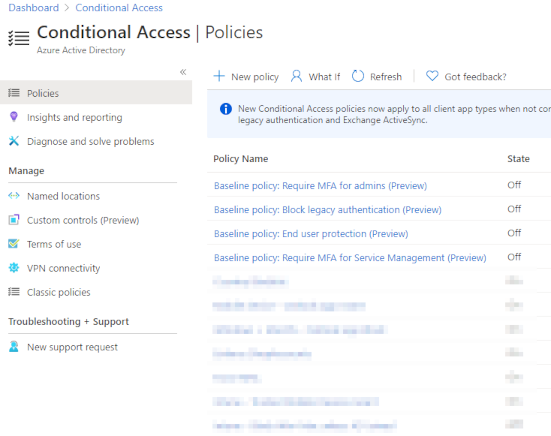
Conditional access is where you can define all sorts of policies that, in the end, determine if a user is granted access to a certain Azure or Office 365 application. There are many criteria you can use. Just a few examples:
- Anybody not in the office should only be allowed access to O365 if MFA was successful. When in the office, always skip MFA and allow access.
- A device not registered in Azure AD should not be able to sync Onedrive.
- Sharepoint may only be accessed from your corporate HQ, unless the user is a member of the Sales department.
- Teams may not be used when the user is not in the USA.
- A login attempt from China is always blocked.
- … many more
Available MFA options
For Conditional Access, it doesn’t matter what factors are satisfied, as long as the outcome is an ok MFA. The available options are:
PASSWORD +
- Call to phone
- Text message to phone
- Notification through mobile app
- Verification code from mobile app or hardware token
An administrator can enable or disable each of these methods. A user can select his preferred method via https://aka.ms/mfasetup but this can be overridden during each login attempt. Of course, a user must have added the relevant information to his or her profile before they can be used. The first time a user logs in where MFA is required, this information is requested from the user.
Re-register MFA
What to do when a user changed phone numbers and did not update his settings? Access via MFA is no longer possible so this requires an admin to assist. Via the Azure user panel, an admin can manually change the phone number or clear all settings and require the user to register again.
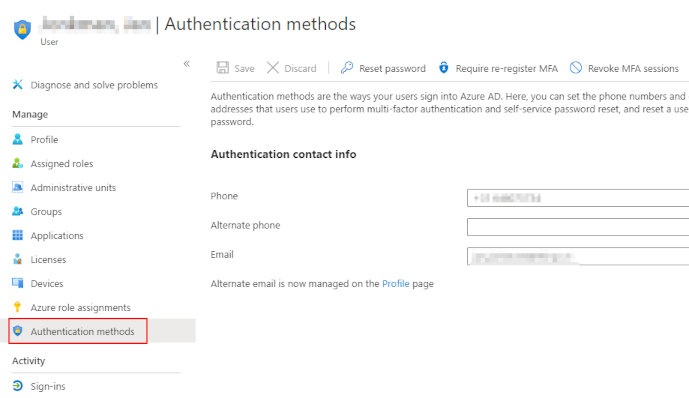
Security warning: be aware that changing or removing MFA settings should be considered a privileged and sensitive task. Proper user verification should be performed to make sure no unauthorized persons can request an MFA reset for an account.
I hope this post was useful for you.
