As an admin, you know how Microsoft is casually working on improving the Office 365 services. This is done not only by adding new features but also by improving and changing existing services. Not all changes are obvious. One of the changes made at the end of 2020 has caught many O365 admins by surprise. Microsoft has changed the way an admin can block automatically forwarded e-mail from your tenant to external addresses.
Why forwarding email to external addresses is dangerous
Basic security guidelines teach us that you need to prevent auto-forwarding. First, because it is a commonly used tool by criminals to unknowingly send email to themselves to learn about the company, intercept passwords or procedures, and more. Second, there are implications of having company e-mail outside of your environment. It means you are no longer in control of it. It can be scanned, archived beyond GDPR limits, leaked, lost, sold, and whatnot.
How to protect users from forwarding their mail
If you set up your tenant in or before 2020, you will find you have by default a Mail Flow rule (in Exchange Admin Center) that blocked all emails following a mailbox rule or forwarder with an external address as the target.

This rule is no longer effective. It does not work anymore in all cases.
Microsoft moved this setting away from the transport rules and put it in the threat management policies. This is found in Protection Center -> Threat management -> Policy -> Anti-Spam. To get there directly, follow this link.
To add, modify, and delete outbound spam policies, you need to be a member of the Organization Management or Security Administrator role groups.
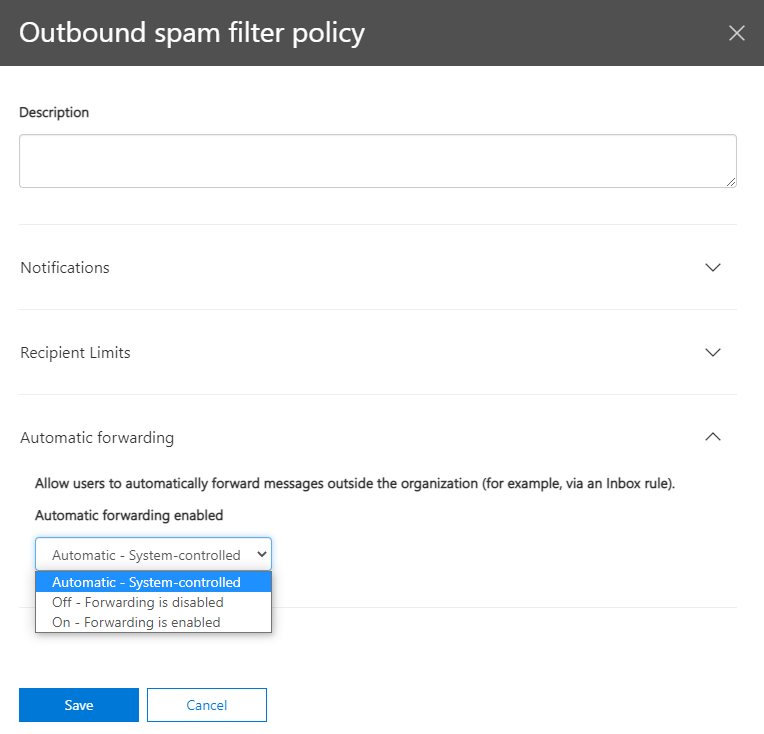
Once opened, you will see a new default policy called the outbound spam filter policy. You can not remove this policy.

This policy blocks the auto-forwarding of email by default, but you can make adjustments to the policy.
The following types of automatic forwarding are available in Microsoft 365:
- Users can configure Inbox rules to automatically forward messages to external senders (deliberately or as a result of a compromised account).
- Admins can configure mailbox forwarding (also known as SMTP forwarding) to automatically forward messages to external recipients.
Disabling automatic forwarding disables any Inbox rules (users) or mailbox forwarding (admins) that redirect messages to external addresses.
A block in this configuration overrules the “Remote domains” setting that allows (or blocks) automatic email forwarding to some or all external domains.
Note that automatic forwarding of messages between internal users isn’t affected at all by the settings in outbound spam filter policies.
Enabling the auto-forwarder
If you want to re-enable the forwarding feature you can change the policy. You have three options for this particular setting:
- Automatic: Automatic external forwarding is blocked. Internal automatic forwarding of messages will continue to work. This is the default setting.
- On: Automatic external forwarding is allowed and not restricted.
- Off: Automatic external forwarding is disabled and will result in a non-delivery report (also known as an NDR or bounce message) to the sender.
Non delivery
When a message is detected as automatically forwarded, and the organizational policy blocks that activity, the message is returned to the sender in an NDR that contains the following information:
5.7.520 Access denied, Your organization does not allow external forwarding. Please contact your administrator for further assistance. AS(7555)
