Your Microsoft 365 sharepoint admin or global admin can set configuration that disables Onedrive syncing of files on computers that are not domain-joined to a known domain. This prevents non-company devices from syncing data. The admin can set which domains are to be allowed by whitelisting their GUID.
How does it work
You can find the GUID of a domain by entering the following command from a domain joined device (workstation or server) with Active Directory PowerShell Module installed:
Get-ADDomain | fl ObjectGUIDThis will return a value like xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx. As an admin, you can then enter this value in the OneDrive sync configuration in the Sharepoint Admin Center. If you have multiple domains, you can enter multiple values, each on its own line. Clients that have joined a domain that is not listed here or are not domain joined at all will be prevented from syncing OneDrive data. This feature works with on-premise Active Directory domains only.
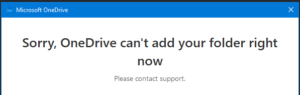
If you try to set up OneDrive on your (private) computer or any device not joined to those domains, you will get a very unhelpful error message “Sorry, OneDrive can’t add your folder right now. Please contact support.“
How to bypass the sync restriction
It appears the OneDrive client is not very secure in determining if your device is domain joined. In fact, the whole check is not about the GUID at all. The check can be bypassed by inserting a GUID or any other value in the registry in the OneDrive configuration that matches a value or GUID that is configured by the admin. You can put in any value, as long as the values in the Admin portal and the client match. In a normal situation, Onedrive will automatically fill in the domain GUID when it finds it is part of a domain.
Quit OneDrive. It must not be running. Create the following registry path: HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\OneDrive, and you add AADJMachineDomainGuid as a String value (REG_SZ) which contains the value of the desired GUID.
New-Item -itemtype directory -path "hklm:\Software\Policies\Microsoft\OneDrive" -Force
Set-ItemProperty -Path "hklm:\Software\Policies\Microsoft\OneDrive" -Name "AADJMachineDomainGuid" -Value "xxx" -ForceStart OneDrive. You will now be able to configure and bypass the sync restrictions, and your OneDrive client will happily sync.
The name of the registry key hints that the purpose of this workaround is to allow managed Azure AD Joined devices to sync in cases where a local domain is not available. However, this functionality was, in time, surpassed by the feature Conditional Access.
What you can do as an admin
The way of restricting OneDrive access using this setting is the legacy way of doing it. Once your company is migrating to a modern workplace, introducing Azure AD joined devices, and maybe people are bringing BYOD, you will most likely reach that point where you want more control over who is accessing your data, from where, what type of device, etc. Ideally, it would be best if you were using Conditional Access and Intune to control access to corporate data. Conditional Access will be evaluated before the legacy setting and is able to block devices that try to use this workaround.
