You can use “per-user MFA” which is part of the free Security Defaults settings. For more granular controls, you should use Conditional Access policies to define exactly when to request MFA.
Once per-user MFA, or Legacy MFA, is enabled, users will be required to provide a valid MFA response for their logins. An administrator can make exceptions for client IP addresses by adding IP address ranges to a trusted IP list. The trusted IPs feature of Azure AD Multi-Factor Authentication bypasses multi-factor authentication prompts for users who sign in from a defined IP address range. The trusted IPs feature requires Azure AD Premium P1 edition. There’s not much else to configure, so as an admin you can’t define your own rules to control the behavior.
Benefits of Conditional Access
While the legacy MFA does the job, it is a fairly black and white situation. Using Conditional Access you can bring all kinds of variables to the table when evaluating a login and determine if MFA is required. Some examples are:
- Which Microsoft 365 or AzureAD Applications the login is for
- Country of origin (without manually listing the IP blocks)
- User risk and sign-in risk threshold
- Device platform (mobile, laptop, …)
- Browser access or actually installed app
- Intune status
- Session length (how long ago was the previous MFA request)
- and more …
So basically all companies that are big enough to have at least Azure AD P1 licenses can benefit from moving the MFA controls towards conditional access.
In your Conditional Access rule you setup all conditions, and finally you grant access with the MFA option, like below:
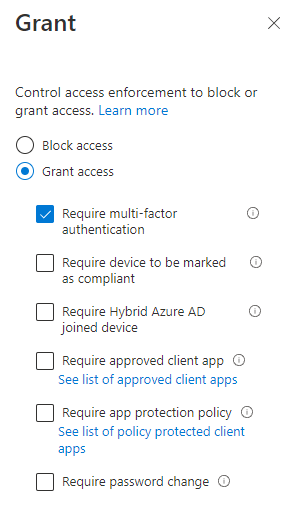
Transition to conditional access
If you have a large number of users configured for legacy MFA that setting will still kick in on top of what is configured using Conditional Access. So, you users may end up with legacy MFA requests each time while your conditional access policies would not have triggered it. The obvious solution is to, after you have enabled Conditional Access, to remove the per-user MFA for all users. Unfortunately, the Azure Portal does not allow for a user-friendly way to do so. Powershell can save you a lot of time.
Per-user MFA can be set to three values:
- Disabled – No MFA will be required at any time.
- Enabled – The user is enabled for MFA but can still use their password for legacy authentication if enabled in the tenant. If the user hasn’t yet registered MFA authentication methods, they receive a prompt to register the next time they sign in using modern authentication (such as via a web browser).
- Enforced – The user is enabled for MFA and can no longer use legacy authentication. Users who complete registration while in the Enabled state are automatically moved to the Enforced state.
Transitioning to Conditional Access requires the per-user MFA to be set to Disabled.
The following script allows you to set the value to Disabled for all users in your directory.
### Function that sets the MFA status
### MSOnline module is required
function Set-MfaState {
[CmdletBinding()]
param(
[Parameter(ValueFromPipelineByPropertyName=$True)]
$ObjectId,
[Parameter(ValueFromPipelineByPropertyName=$True)]
$UserPrincipalName,
[ValidateSet("Disabled","Enabled","Enforced")]
$State
)
Process {
Write-Host ("Setting MFA state for user '{0}' to '{1}'." -f $ObjectId, $State)
$Requirements = @()
if ($State -ne "Disabled") {
$Requirement =
[Microsoft.Online.Administration.StrongAuthenticationRequirement]::new()
$Requirement.RelyingParty = "*"
$Requirement.State = $State
$Requirements += $Requirement
}
Set-MsolUser -ObjectId $ObjectId -UserPrincipalName $UserPrincipalName `
-StrongAuthenticationRequirements $Requirements
}
}
### Call the above function for all users
Get-MsolUser -All | Set-MfaState -State DisabledModern authentication
Please remember that Conditional Access requires modern authentication to evaluate. Therefore, using Conditional Access to enforce MFA also requires modern authentication. Please make sure that your tenant and your applications are using modern authentication and not legacy authentication anymore, or they will fail to authenticate. Legacy authentication is no longer enabled by default since 2019, but it may be re-enabled in specific cases.
